There is a good chance that you are reading this page because you have just noticed something strange on a Google Results page.
This can be worrying to see when you are surfing the net, and even more worrying if it is your own website that this message is appearing under!
I built this page so that if someone finds themselves in a similar situation as I did once, they will have an easy-to-navigate and accurate source for the many questions that they will naturally have.
I hope that if you are in the unfortunate situation of recently discovering that your website has been hacked, this page may bring you a certain level of peace and understanding, whilst also assisting you to solve some of your more immediate problems.
The Story Behind This Blog
When I was early in my career as a marketer, I was on the receiving end of a hack.
This is not uncommon in this day and age.
I had moderate technical ability at best and was not prepared for this to happen.
The next 14 hours of my life were a hectic and scrambled rush for information, understanding, and assistance.
I was an employee at this stage, working on a company’s website.
My chief workload was:
- Content creation
- Social media management
- Search Engine Optimization
- Basic WordPress Management
One thing that occurred differently for me, was the fact that even though Google had placed the “this site may be hacked warning” on the SERP results for the website, we did not actually have any warning messages inside our Google Search Console.
This unique problem became quite frustrating for me, as a majority of the resources that I could find were based upon the presupposition that there would be a message within the site security panel of the Google Search Console.
Other challenges I faced included:
- Most support content online seemed to be aimed above my technical knowledge
- No existing direct line of communication between myself and the webhost
- The fact that this happened on a Friday
Fixing the site hack was a significant turning point in my career, and also one of the most harrowing days that I’ve ever had in an office.
Just remember, this is not the end of the world.
Some of the posts that I have put together on this blog will:
- Help you work out why your site has been hacked
- Assist you in figuring out how they did it
- List out the various steps you will need to take
- Walk you through what happens next
- Are You Panicking? Losing Money?

You are going to be ok.
If you don’t believe me just yet, that is completely understandable. You have just found out that your website has been hacked after all.
However, you need to remember that when you are panicking, you are pushing yourself further and further into a state of shock.
When you operate in a state of shock, you make quick, poorly thought out and often rash decisions.
Take a moment to draw in some context to the situation, and focus on the perspective.
Yes your website has been hacked.
No, it is not the end of the world.
Yes, this is a serious inconvenience.
No, it is not something you cannot recover from.
You may feel all alone at the moment, and as though the whole world is against you.
This will pass.
You need to understand that being hacked is almost like a rite of passage for website ownership.
At the end of the day, if you weren’t building a good quality website, they would not have hacked you anyway.
I wrote this section so that you would be able to:
- Get some context
- Understand the why and what
- Have some solid objectives to act upon
Remember, your webhost, your co-workers, and your SEO provider are all in this with you. Everyone is going to have to play their part from here on.
Allocating Blame
You may find yourself asking who’s fault is this.
Trying to rigorously assess who in your team let you down by leaving a door open, or who was supposed to have set up the web security protocols, and what not.
This is not a helpful attitude for you to embrace today.
When everything is resolved, you will most likely be writing up reports, and then you can work out where the intruders gained access, or where your defense was lacking.
For now, you need to focus on the task at hand, getting your site clean and back up.
Note: allocating blame is a separate process to figuring out how they got in. It may very well be that you discover they gained access through one particularly vulnerable employee’s credentials. This is not the time to blame that employee however, this is the time to get your site clean again.
Are You Losing Money
This is one of the first things that may be going through your mind. For many people and businesses, their website plays a strong part in their livelihood.
I will however begin by saying, before you start asking if you are losing money, you need to ask yourself:
“is my site compromising credit card details or the online safety of my users?”
If the answer is a yes, then you need to switch your focus from your own financial impact for the short term, and make sure you:
- have the site quarantined and
- begin the process of working out what data has been compromised and
- who you need to contact.
Once you are sure that your site is no longer posing a clear and real threat to the larger online community as a whole, then it is time to start figuring out whether you are losing money from this hack.
How does your site generate revenue?
There are a few ways that a website can be a revenue generator, and depending on how your operation has been set up, you may stand to lose more from the hack than others.
Sites may be generating revenue from:
- Affiliate Programs
- Advertising Displays
- Being the online presence of a real world business
- E-Commerce
- Selling Links or advertorials
Each of these revenue streams will be interrupted in their own way.
Affiliate programs and advertising displays
require a user to trust the links on your website enough to click on them and be taken to a vendor’s site. If your site is suddenly filled with spammy links for Viagra, this will reflect badly for all other advertising that is placed on your site.
Not only that, depending on the contractual arrangement you have with your vendors, they may learn of your hack and decide that they do not want their sites advertised on yours any longer.
Being the online presence of a real world business
is a complex issue once again. The level of financial loss is dependent on how reliant you were on your website to generate leads for your sales team, how quickly you respond to the hack, and what type of hack it was. The website I was managing when I was hacked was this type of website.
Selling links or advertorials
I am not here to judge you. You are already breaking the Google webmaster guidelines and one would assume that you knew this when you began operating. The chief problem you will be facing now, is that your site’s hacking has generated serious attention to it and is likely exposed for what it is. Not only that, if you relied upon having a quality Domain Authority and Trust Rank, then this is likely to be damaged at least in the short term. Having damaged metrics will mean you can no longer request as large a payment for your links, as they have just become less valuable.
Traffic Loss and Its Relation to Revenue
Losing traffic is the first way that this hack stands to reduce your revenue. Less people viewing your site means less advertising money, or less customers who may decide to purchase from you.
Organic Traffic Loss
Assuming your website is not compromised with malware (in which case a red page will come up for any user about to access, warning them that they should reconsider), then you primarily stand to lose out on organic traffic to your website.
As users find your website listed in the SERP they will see the warning that the site may be hacked, and they may reconsider going to your site.
Not only will this affect the click through rate (CTR) of your listings, you will also find that your website is slowly (or maybe even quickly) declining in the rankings for your key words.
In my experience, I was honestly surprised that the CTR did not drop further whilst we were displaying the “this site may be hacked” message on the SERP.
I am unsure if the average user either did not notice it, or did not care.
I suspect this may be the reason that for very serious malware threats the user is presented first with a SERP warning, and then if that is not enough to keep them safe, they are presented with a giant red page telling them that it is a horrible idea to continue.
Note: If you are not serving malware, and a majority of your traffic is coming from social media, you do not stand to lose as much of your traffic as if you were relying upon Google search results for traffic generation.
Rankings Loss
We went from sitting at the 1st position for our main keyword, and then sunk to about the 7th position very quickly.
The rankings loss was only temporary and once we cleaned the site and did our own version of requesting a review (We did not have a Search Console Security issue warning), everything went back to how it was before the hack.
It helped that we acted quickly, and it helped that I had spent an entire day working out exactly what we needed to do.
One of the actions I needed to take, was to clean up a massive group of spammy backlinks that were now pointing directly at us.
The hackers had decided that even though we had some great Domain Authority and Trust metrics, that it wouldn’t hurt to give it a little nudge with some additional inbound links.
They had pointed a reasonably large amount of really low quality links at our home page.
The Google Search console has a tool that allows you to go in and manually disavow any spam links that are directed at you. If you have never used the disavow tool, then treat it with caution. You may want to consider having an SEO professional assist you with the link audit and disavow process.
Potential Trust Loss
There is no denying it, when a member of the public finds out that you have lost control of their personal (or god forbid financial) data, they will lose trust in you.
The way you conduct yourself after this hack will play a large role in whether people go on to trust you again, or if they simply move on and find a new supplier or website to engage with.
If you have lost personal data, notify people. It is better than having them find out from some other means, and it will help to show that you are a transparent and honest webmaster who fell victim to a crime.
Let people know what steps you are taking to ensure that this is not going to happen again.
If you can afford it, perhaps consider gaining some assistance from a professional PR firm.
If you cannot afford a PR firm, then you just need to show people that you were a victim, and that you are working your hardest to make things right.
Direct Costs Associated with Detection, Quarantining, Cleaning up and Recovering from the Hack
As much as a healthy dose of retrospect is not what you want to hear right now, prevention is always better than a cure.
I am sure that next time you are going to be more prepared and that you will now realise the importance of preventative maintenance and infrastructure.
In the mean time, think of it like this.
If you drive a car, and do not regularly make sure that it is serviced, topped up with oil, and generally maintained; you may feel like you are saving money and effort.
However, when the car finally does break down, the costs associated with towing it from wherever it let you down and then fixing it, will be considerably higher than the costs that would have been associated with keeping it maintained from the word go.
I learnt this exact lesson about cars when I was a teenager. It was not until I suddenly had to send a car to the wreckers rather than foot a giant bill to fix my neglected engine that I finally realized the cost benefit scenario of preventative maintenance will always beat the cost benefit of only having an expert investigate after a problem.
If you do not currently have anyone looking after your website security, there is a good chance that this has helped the hackers win this time.
Paying someone to come in and fix it will always be more expensive than paying someone to help make sure this doesn’t happen in the first place.
Likewise, even if you are not paying for someone to help fix it or paying someone to help prevent it, think about your time.
A small commitment each week to maintain security on your site will likely be less time consuming than the process you are about to commence.
Not Technically Skilled But Still Want to Help?
Not a Web Dev or Site expert, You Can Still Help

You may be worried that you do not have the correct skills required to be of much assistance in this process.
I have purposefully written this entire blog with you in mind, and endeavored to not write above the heads of anyone.
I hope that in this time of crisis you will be able to find comfort, support, and inspiration for how you can get through this set back.
Just remember, no one has technical experience in bouncing back from a website hack the first time it happens to them!
I would encourage you, regardless of how you view your skill set, to read through this page and see what you can do; even if it is just biding time and easing tension whilst waiting for the cavalry to come help.
How Can You Still Be Useful with a Non-Technical Skill Set
This is a very fair question you may be asking yourself.
I know when this happened to me, my first response was “there is so much that I need to learn, and I need to learn it NOW!”
This is not particularly realistic.
Advanced skill sets in handling hacked websites are not something you will gain today, even with the best Google-Fu.
When my site was hacked, my skill set was not particularly technical, yet I managed to play a helpful role in the cleaning up of the site.
If you jump to the section about discovering what the hackers have done, there are some very simple and easy to use steps on how you can help to identify the changes that the hackers have made.
Other ways you can help get through this are:
Project Management
You are no doubt going to need a series of professionals and service providers to get this all fixed, you are the one that discovered the problem and have initiated the clean up process.
It is your job to oversee the broader project of “getting this site healthy again”.
You are the go between, the communication relay, perhaps even the gopher.
Suffice to say, you will find ways that you can be of assistance to this process.
Giving Access Credentials To Experts
This may seem like an odd one, but if you have had to bring in an additional service provider (such as a dedicated website hack recovery team) then you will most likely be the one that needs to be giving them access to such areas as:
- Google Search Console
- Cpanel
- FTP
- Name Server Changes
- Your CMS
Remember, don’t give these credentials to just anyone.
Ironically over sharing of these credentials may have led to the problems in the first place.
What Do You Need to Do First?
Sounding the Alarm

If you have just found out that your website has been hacked, it is time to sound the alarm and get all the reinforcements you can.
Depending on the site, and what your role is, there may be a lot of people to contact, or there may be only a few.
Contacting Your Webhost
One of the first people you will need to contact is your webhost, they are the ones that will be able to help you with a lot of what is going to be needed in the coming hours.
Depending on the hosting package you have, you may need to submit a support ticket, send an email, register for a live chat or be able to give them a phone call.
In situations like this, you realise just why it is often worth paying that small amount extra in order to make sure that you have direct phone support, rather than simply email support.
Once you are in contact with your webhost, they will more than likely have an action plan in place for situations such as these, and they will often become that reassuring third party that will help you know that everything is going to be ok.
You will need to give them as much specific information as possible, yet not overload them with unnecessary information.
This initial contact is just enough for them to start their action plan rolling. They may also need to investigate their own servers (particularly if you are on shared hosting) to make sure that a) there is no threat to other customers, and that b) the threat has not come to you because of another customer.
Contacting your Boss and Co-Workers
If you are working on your own, then you will obviously be skipping this step.
If you are working in an organization that has many people who work on the website, or who’s work is influenced by the website, then it is important to let them all know that the site has been hacked and that steps are being made to bring it back to safety.
You may be hesitant about telling your boss, but you need to remember that this is not your fault!
Your boss may need to get ready for some additional contractors to come in and help with the clean up, as well as the fact that you do not want your boss to find out from another source and then ask you why you did not inform them.
Sounding the alarm and getting all hands on deck for the cleanup is far more important than trying to keep a problem concealed until a solution has been found.
Contact your SEO Supplier
If you have an agency or a contractor, or even an employee, whose primary role is maintaining the SEO for your website, then bring them into the fray early on.
Depending on the type of hack that you are experiencing, they may have a great skill set to be able to assist in the discovery and removal process of any changes that have been made to your website.
It is also likely, that they may be one of the few people who have regular access to your Google Search Console, as this is primarily a tool used for SEO professionals to assist with their job role.
Web Security Professionals
I will go out on a limb and assume that since this hack occurred, you probably do not have a web security provider that pays regular attention to your website.
One myth that may be worth dispelling now, is that web security is an inherently expensive product/service that is only really necessary for large websites that house very important or sensitive data.
As you can now see, even smaller websites face security threats.
I would strongly recommend that you reach out to some professional website security providers and have them assist you with the coming tasks.
They will then also be able to greatly assist you in the process of setting up a better line of defense against these types of attacks occurring again.
This situation kind of reminds me of when I avoided taking my car in for a service for a very long time, right up until it finally broke down on me.
The mechanic quite rightly pointed out to me that any money that I thought I was saving at the time, was instantly lost due the fact that prevention tends to be far cheaper than a cure.
Maintaining Communication
As each of these professionals and individuals start their work to fix the website, it is important that everyone stays in communication with one another. For example, if your SEO finds that there are malicious spam links in a certain folder, then everyone should be updated as to the changes that have been found.
Information such as this will help everyone else in determining what needs to be done next.
Notifying Affected Parties
This is certainly something you are not going to enjoy. If you have lost personal or financial information for your users, you have a duty of care to let them know. Likewise, if your company has a board of directors or shareholders, you have a responsibility to let them know. You will also need to let your manager or boss know also.
For financial data loss, you will need to let the users know as quickly and directly as possible; and you will also need to let your credit card processors know that you have had a breach.
For personal data loss, you will need to let your database know as quickly as possible.
Depending on how severe the data loss has been, you may wish to seek some professional assistance from a PR firm.
The next thing you will need to do is check Google Search Console.
Alarm is Sounded, What is the Next Step?
Checking Your Google Search Console

One of the first things that you will need to do after you sound the alarm, is to log into your Google Search Console.
If you do not know what Google Search Console is, there is one of two options here.
One, someone else on your team will have access.
Two, you have never set up Google Search Console.
The people most likely to have access to the Google Search Console are:
- Whoever built the website
- Your SEO supplier
- Your boss or other colleagues
You will need to check if there is anyone who already has access to the search console.
There is every chance that someone will already be in there due to the fact that you raised the alarm.
If you find the person who has access to Google Search Console, then you can request that they share access with you.
If you discover that no one has previously set up Google Search Console, then you can find detailed instructions from Google here.
Google will be able to step you through the processes, it involves registering for Search Console, as well as a verification process in which you show Google that it is in fact your website.
Note: there is a chance that the hacker will have registered Google Search Console for your website and adversely affected your site. Google will be able to help you through this process, and more information can be found in the Google Support for Hacked Websites tutorials.
Checking your Google Search Console for Security Issues
Within the search console there is a tab down the left hand side marked “security issues”.
This is the area of the console that Google will communicate with you about why they think your site may be hacked, and what they think you need to pay attention to.
Once again, Google provides some great tutorials that you will be able to use to help you through this process.
This is also the place where you will be able to resubmit your site to Google once you have cleaned it up.
Resubmitting the site shows Google that the hack has been dealt with, and it should stop placing the warning message within the SERP results.
What if Your Google Search Console Does not Display any Security Issues?
This was the scenario that I faced when I was first hacked.
I accessed the resource material provided by Google, found it to be quite a bit over my head in a few places, but understood that one of the first things I needed to do was to check the security issues tab in my Google Search Console.
I went ahead and logged in, only to find the security issues panel looking like this:
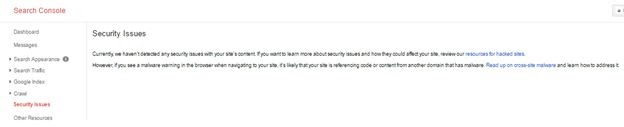
This was perhaps one of the most frustrating experiences of my life.
Google was publicly displaying a warning to all potential site visitors that the website I was working on “may be hacked”, yet not telling me anywhere within search console that they thought my site had been hacked.
Furthermore, I knew from the Google tutorials I had already watched, that a huge portion of the clean up process would be assisted by the information that they were going to give me from within the security issues tab.
Later, after we had cleaned up the site and gotten the hackers out, we realized that the problem was even further compounded, due to the fact that we did not have access to a ‘resubmit button’ to let Google know that we had fixed the problem and that they should stop warning people that we may have been hacked.
All I can say, is that part of the reason I wrote this page, is because finding that security issues tab empty made me feel even more alone and exposed than I had previously.
Never the less, with or without the direct help from Google, you can certainly get the site fixed up and have the message removed from the SERP.
Rather than using the resubmit button within the console, I simply resubmitted the site map, and asked Google to fetch and render the site again.
Who knows if this is the appropriate action, but I do know that the warning message did not stick around long after that.
Alarm, check! Search Console Check! Now?

The next step on this process is going to be a little more technical than many of the others. If you have a team that can help you, this is advisable. Generally your webhost will be able to (or may have already) get a majority of the next step done for you.
The two main things that need to be done before you even start to investigate fixing the hack, is to quarantine your site; and see if you have a non-corrupted back up available.
Quarantining Your Site
In some cases, you may be finding out about your website being hacked from your webhost, as they let you know that they have just quarantined it for you.
I guess in this instance, you don’t need to worry about setting up the quarantine yourself at least.
The primary reasons you will quarantine your site are:
- To remove the core files away from the hackers ability to get to them
- To minimize the damage that is done to the greater public from your hack
There are a lot of opinions out and about regarding site quarantining.
Many people will argue that it is not a necessary step, regardless of whether Google has made it an official step within their site cleanup process.
You may also be facing external pressure from a client, or your boss, to not take the website down.
Times when you may consider not quarantining
You may consider not quarantining if you know that you have a reliable back up ready to restore the site to its pre-hacked form. If you know that you can quickly get it shifted back to a safe and clean state, then you may decide to skip the quarantine.
Note: even the pre-hacked form will require some additional work, because whatever security vulnerabilities allowed the hacker in, will still be present. This means that the hacker may be immediately trying to regain access through whatever route they took initially, during the clean up process. Quarantining would prevent this.
You may also consider not quarantining your site if it is immediately clear that the hacker is primarily focused on syphoning off SEO authority by placing invisible links. Often in this situation you will only be receiving a “this site may be hacked” warning, and not a full “this site may harm your computer warning”.
In this situation, many people are going to opt to fix the problem whilst the site is live. Just remember, this may draw it out to a much longer process than could potentially be the case if you had quarantined the site.
In my perosnal experience, between pressure from on high to not close the website, the fact that the warning was only a ‘this site may be hacked’, the absence of a search console warning, and the fact that I quickly found the spam links; we decided not to quarantine.
Times when you absolutely must quarantine
If your site is distributing malware, or you have the warning stating that “this site may harm your computer”, then you must quarantine it. It would be unethical for you to potentially allow more people to receive malware just because you wanted to keep the site live whilst you dealt with the incursion.
What does quarantining a Website Entail?
Quarantining a site is setting it up so that the host your website files are stored on, can no longer serve content to users.
Your webhost may have a specific way that they set up a quarantine in this situations, often the folder will be marked “quarantined” and you will still have access to the files so that you can repair and clean up the damage.
One method of setting up a quarantine is to simply change the DNS of where your domain is pointing, and make it point to a static page on a different server and have it deliver a 503 HTTP response code.
This is a step that can be done from within the DNS settings of your domain registrar. However, if you are unsure about how to proceed with the quarantine, I strongly suggest that you contact your webhost to have them assist with this.
The 503 response code lets any visitor to the site (bot or human) know that the website is currently down, but that this is a temporary problem and that they should check back later.
Website Backups and Potential Restorations
One of the quickest ways that you can get your site cleaned and operational again is to restore it from a backup. Ideally, you would have a recent backup from a time prior to the hacker gaining access to your site.
It is important to note, that your backup should not be coming from the same database as your website. Backups should be stored on a separate database, otherwise you run the risk of having your backup infected at the same time as your website, thus rendering it useless.
Many site owners keep their backup with their webhost, if this is the case then you will need to work with your webhost to:
- Ensure that the backup is from a point in time before the hack
- Ensure that the backup is not corrupted also from the hack
- Restore the backup version of the site to the live version
Note: simply restoring a backed up version of the site will not prevent this from happening again.
If you simply restore from a backup, resubmit to Google that your site is clean, then this leaves the door wide open for the same hacker (or another hacker) to simply walk straight back in.
You do not want to get into a long standing game of whack-a-mole with the hackers.
Take the time to clean up your site, remove outdated plugins, review all user access points, and ensure that you are better prepared for next time.
If you do not have a backup
Retrospect never helped anyone. This is not the time to be angry at yourself or your company for not having appropriate measures in place.
If like many webmasters, you assumed that no one would ever want to hack your website, then it would make perfect sense to have not spent the time ensuring security protocols and making sure that you have backups prepared.
You can still clean your site up, you can still close the security holes, and you can still get back on the road.
It may take longer without a backup, but this extra workload now will help to make you more vigilant in the future.
When our site was hacked, we did not have an appropriate backup in place.
This meant we had to clean up the site from scratch and did not have the fortune of hitting a semi-magical ‘reset’ button. I feel your pain.
Finding The Changes They Have Made

Depending on why the hackers have infiltrated your site, they will have made some changes to it. These changes are the reason Google has labelled the site as potentially hacked.
Identifying what has actually changed on the site can be the most direct path to understanding why they hacked you in the first place.
Below are some examples of the most common changes that a hacker may have made on your site, some basic ideas for how you can detect the changes, as well as some basic removal techniques.
- Setting up doorway pages
- Setting up a phishing system
- Using Cloaked Pages
- Adding Spam Links
Setting Up Doorway Pages on Your Hacked Site
Doorway pages or parasite hosting is used by hackers to steal the authority of your domain and improve their site’s website rankings.
They create landing pages on your site that are optimised for their keywords, frequently in the realm of viagra or other similar drugs.
Due to the power of your website’s domain name, when these pages are optimised they will shoot to the top of the SERP rankings. Once clicked, they then use a piece of referring code to direct the unsuspecting user to their site.
They also benefit from the appearance of a seemingly respectable website selling their product.
When looking at the Google search results, the giveaway for sites that have a been hacked and have parasitic pages on their domain is the incongruity between the keywords and what the rest of the site is about.
This example clearly shows that the domain name isn’t about the sale of prescription drugs, yet this subpage (as seen below) is about viagra.
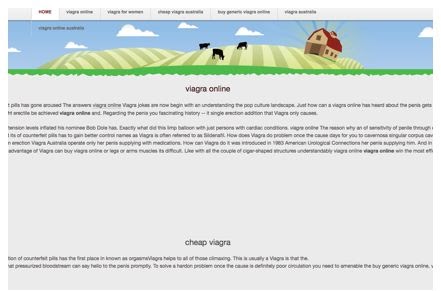
The rest of this site is about the sale of meat products and clearly isn’t a website that would be selling viagra or the like.

An attack such as this requires a comprehensive audit of your site and the deletion of nefarious landing pages.
It can be a time consuming and laborious undertaking and is often best left to a professional.
If you have an uninfected backup of your site, it can often be simpler to simply delete the entire thing and upload it again.
If you wanted to try and find the offending pages yourself, the first place to start would be the back end of your content management system, which should give you a list of all active and draft pages.
For a faster and more systematic scan, you can check all pages on your website by using a tool called screaming frog.
This tool will allow you to automatically check every page that your website is currently displaying, as well as key metrics that can help you quickly check if there are pages present that should not be.
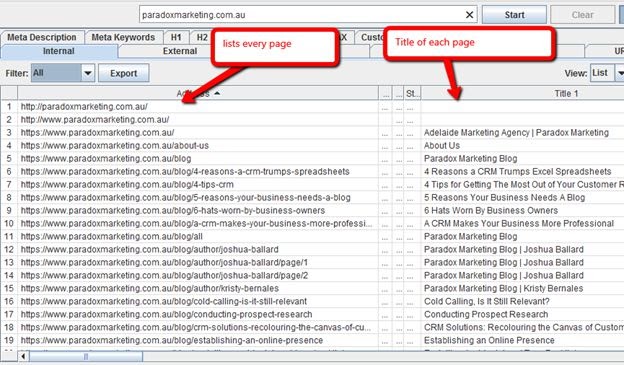
This tool can allow you to do a very quick scan and see what pages are currently present that should not be, as well as seeing what they are all titled.
Once you can see if there are any pages present that shouldn’t be, you can delete them.
Note: the guys who created Screaming Frog (being the legends that they are) have made a basic license free, but this comes with a 500 page limitation. If you need more than 500 pages scanned, you will need to purchase a license.
If you haven’t found any pages that shouldn’t be present, then there are still other changes that the hackers may have made. Further down this page you will see other examples of potential changes that have been made.
Hackers Setting Up a Phishing System on Your Site
Phishing is a form of social engineering, it is the process in which a cybercriminal uses a deceptive email, text message or web page designed to look the same as a trustworthy source.
Generally the false page or email that they display is the login form for various services, such as email, social media, banks, online stores and so on.
The goal is to trick someone into giving them their personal information, log in credentials and so on.
Phishing sites use the appearance of a trustworthy website to trick visitors into submitting their sensitive information.
A phishing site uses a range of tactics to convince the user that the site is genuine.
They can even use the genuine website in conjunction with the fake one to add legitimacy to the deception.
One of the most common tactics for adding a phishing system to a site is using subdomains. They create pages that appear to be the same as your site, however have an extra address element in the URL.
For example, your domain is example.com. The hacker will create a subdomain by adding an extra piece of information, such as phishing.example.com.
This could be as simple as adding a word that appears related to your industry, like repairs.mechanic.com.
It leverages the legitimacy of your actual site to create another path for the user to head down where they will be asked for their information.
This is dangerous because the trustworthiness of your site will give the user confidence that they are providing their information to a site they trust. This in turn will leave them vulnerable to theft and could adversely impact your brand and website in the future.
Often, a Phishing system will be an additional page installation, so you can check for it the same way that you have searched for spammy landing pages being added to your site.
You can also generally rely upon the Google Search Console to warn you which URL’s on your site are suspected of phishing. If you don’t have a Google Search Console security message.
When hackers use cloaking methods on your site
Cloaking is a way of presenting the human user with different information than is seen by the search engine crawlers.
This is a black hat SEO method that can lead to severe penalties and make it almost impossible for your site to rank honestly in the future.
Sending the Spam to Search Engines
It involves presenting one version of the page to the human user that doesn’t include the spam elements and looks as the site would be expected to.
The second version of the page that is seen by the search engine bots is usually heavily spammed with bad backlinks, stuffed with keywords, and often includes text that is invisible to the human eye.
Again, as with other hacking techniques, it is designed to leverage the quality of your site for the good of a hacker’s financial gains.
Feeding the incorrect information to the search engine allows it to rank for keywords that it desires, that have nothing to do with your website.
Sending the spam to the users
The other side of the coin is when they will keep your site sending the same information to search engines, maintaining your authority and trust in the Google ranking systems; yet presenting users with something completely different.
In this scenario, your website could be ranking for ‘cute kittens in San Diego’ and drawing in traffic that is expecting to arrive at a page about adopting a new pet.
However, when the user arrives at your website, they are presented with whatever the hacker wants them to see. Often this is porn, pharmaceuticals and so on.
This method is particularly difficult for a search engine to detect, as it is specifically keeping the version seen by the crawlers separate to that which is served to the users.
In the kitten scenario, you may not actually receive any warnings at all, until someone calls you and complains about the fact you served their family pornography rather than kittens.
Checking if cloaking is being used
In order to check and validate that the same version of the page is being served to humans and bots alike, you can use the Google Search Console.
You can visibly inspect the page and see what is being served, and then use the Search Console to “fetch as google and render” in which case they will show you the version of the web page that they are being fed next to the version that a user would see.
Here is an example of me using search console to fetch and render the front page of my agency’s website.
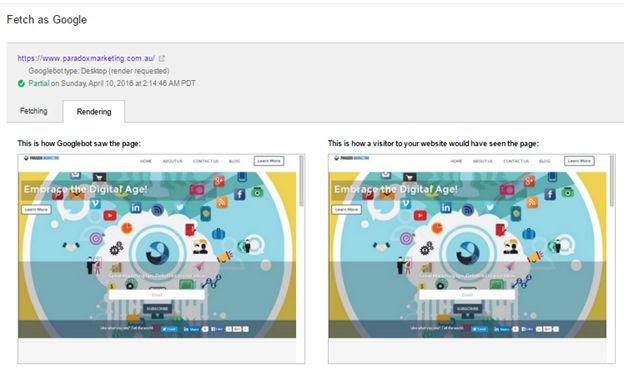
Dismantling a cloaked page can be a rather advanced undertaking, and may be best off left for the professionals.
When Hackers Add Links To Your Website To Try and Rank Their Site Better
As I described in the section about covertly and overtly using your website to further advertise and market theirs, this process is completed in an attempt to make Google favor the hacker’s website better in the search results.
This is the type of hack that I was on the receiving end of early in my career.
The hackers placed a huge amount of links to their own website, right inside my company’s website.
The principle behind this, is that when one website links to another, it is essentially vouching for it and this indicates to Google that the linked to website is quality and should appear higher in the SERP.
Where are they most likely to place the spam links?
When my site was compromised, the spam links were placed within the header and footer of the website.
To be more specific, they were inserted into header.php and footer.php within our wordpress editing tool.
The reason a hacker would choose the header and footer, is the fact that these two areas of the website are visible on every page.
Every page on the site displays the same header and the same footer for the entire website.
They placed approximately 60 links, which was then multiplied by approximately 350 pages, giving them roughly 21,000 links back to their own website.
In the black hat world, link building is typically about quantity, and rarely about quality. In which case, whoever hacked my site must have been pretty chuffed with the 21,000 links they “built” that day.
What will the links look like once discovered?
The links themselves will often be in a tiny font, and have the same color as the back ground on which they have been placed.
This is done specifically to make them less detectable when someone looks at the webpage.
When you discover them, you will be able to see that they are almost guaranteed to be using anchor text heavy key word terms.
The anchor text is the words used for the link, for example if I was to link to http://en.wikipedia.org I could do it just like that, or I could write it like this: the oracle of all human wisdom combined.
Either way, the link is going to the same place.
In the first scenario:
The search engine can see that it is a link for something in English (the en gives this away) called Wikipedia that is run by an organization (.org).
In the second scenario:
The search engine gets all of the same information that it did from the first example, plus learns that another word or phrase that essentially means the same thing as Wikipedia is “the oracle of all human wisdom combined”.
It also tells the search engine that this is essentially what that website is, and what can be expected on the other end.
Your spammers will have made the anchor text of the links the same as whatever keywords they are trying to rank their website for.
In my situation it was “NFL Jerseys” “Cheap NFL Jerseys” “Discount NFL Jerseys” and so on.
The idea being that when an end user jumps onto google.com and types in “cheap NFL jerseys” the search engine has the impression that these keywords relate to the website that the spammer was trying to rank.
If this doesn’t make sense, don’t worry; it really doesn’t matter that much to you right now.
How to Find The Hidden Links
If you know that the links are most likely going to be found in your header.php or footer.php files, you may be tempted to look there.
This is probably going to take you a lot of time, and it also may not be where they have put them (if there are spam links to be found in the first place).
I used a program called Ahrefs to alert me to the existence of the external links.
However, I could have just as easily used the free program discussed earlier, the Screaming Frog SEO Spider.
Within the Screaming Frog dashboard, you can select “external” to show you a list of outgoing links from the site.
These methods will allow you to check what pages the links are coming out of, but they may not help you find exactly where they are on the page.
Finding The Hidden Links Exact Location On The page
I used (and would strongly recommend) a free Google Chrome Extension called “Link Miner” by Point Blank SEO
This extension allows you to quickly scan any webpage, and it will highlight any links that are present.
You get a little icon in your chrome panel. It will always update and let you know instantly by looking at it just how many links are on any given page.
When you click it, every link will be highlighted, details are placed next to the links, and then you can download every link into a csv file.
I used it to highlight and discover the spam links hidden in the header section and footer section of the site I was working on.
This is how I realized the links were written in white on a white back ground:

This is what the site header looked like once I hit it with the linkminer extension.
Why was it beneficial to see them?
Whilst I could have searched for them in the php files for every page showing them as being an external link, this would have taken a long time.
Once they were highlighted, I could see what the anchor text was, and then when I went into the php editor to remove them, I was able to hit ctrl+F and search by the anchor text term.
Once you find the links, you can remove them.
If it was just links causing the “this site may be hacked” warning, then you can resubmit to google and attempt to have it removed.
Beware however, if you don’t close whatever door the hackers came in, then they will just replace the links.
Reasons They May Have Hacked Your Site
Depending on your site, there are a range of things that a hacker may have been trying to do. This list is by far not exhaustive, but it outlines some of the chief motivations or reasons that a hacker may have.
Generally these motivations come from a financial perspective, though this is not always the case.
You may be surprised to find that there are more ways hacking can make money than simply credit card theft!
Stealing or Accessing Data
One reason that a hacker may target a particular website over another, is if they are trying to steal or access private data. When you hear of large scale hacks on the news, this often the motivation. A recent example would be the hack on the adult site Ashley Madison. In this hack private user data was stolen, which compromised the identity of their entire user base.
When you are trying to assess whether data access was their principle motivation for the hack, you will probably ask yourself the simple question of “what data did they access?”
The reality is, this is not always clear. It can take considerable resources to track the data flow through a website and to see what the hackers may have accessed or removed.
You must operate on the assumption, that all data stored on your website core files will have been compromised.
You will need to determine what data was being stored on your website core files, and act accordingly.
Personal Data (non-financial)
If for example you keep user data on your core website files (aka on your server), such as:
- log in credentials
- email addresses
- other personal information, such as names, phone numbers
Then you will have an ethical responsibility (and in many jurisdictions a legal responsibility) to notify the entire user base of the potential data breach.
This is especially important, due to the fact that any users ‘recycle passwords’ across multiple platforms. Which means that their associated email address and log in password to access your site, may also be their email and log in details for many sites.
If you feel that this is embarrassing, then take a moment to reflect on 2014 when Ebay had to send out a very similar email warning their customer base of the need to update passwords across all platforms due to a hack.
If you are using a 3rd party form provider, or CRM, then there is a very good chance that any user data collected will not have been breached. You will need to contact your form provider or CRM provider in order to validate whether the data would have been vulnerable.
In many cases, the data is captured by a widget on your site, and sent directly to the third party website. You will need to find out if any personal details entered onto an embedded form will have also been saved (temporarily or permanently onto your website core files).
Note: If your website uses an accounts based system, in which a user logs into your backend, then you will definitely need to notify all users of the data breach.
Financial Data
First of all, if you are currently accepting financial data (credit card details) directly onto your own website, and not redirecting to a third party trusted website (paypal, a bank’s payment gateway, and so on) then stop immediately.
I know this does not help you now, as you look down the barrel of potentially having lost credit card details for every customer, but the hard truth is that you realistically should have never been allowing customers to key in credit card details directly onto your website in the first place.
I don’t care if the fees are higher for using external card processors, those higher fees are in place to help pay for complex and expensive security measures to be put into place.
It is now your responsibility to notify EVERY customer that it is time for them to call their bank and cancel their card number. This does not mean send them an email, emails can be missed or forgotten. Call them.
You need to also tell your bank (or whoever it was that you had doing the final processing on the cards) that you have had a security breach. They need to know, and they can help other financial institutions cancel the stolen card details quicker.
Yes, this is embarrassing for you. I can however guarantee that this will be a very steep and sharp learning curve for you.
No, your SSL certificate does not mean you are in the clear.
Just remember, this also happened to the Target retail giant, people may blame you for your negligence, but as long as you try your best to make things right, you may not have lost a customer forever either way, this should not be your primary concern right now.
You may want to consider hiring a PR agency to help get you through this at a later stage, for now you must focus on the task at hand.
Setting Up a Phishing Scheme
I have gone into greater detail further down on how to check for a phishing scheme operating on your website.
In terms of why they would set up a phishing scheme, it is enough to simply say that they are using your website as a means to collect personal and potentially financial data from users. The dynamics are a little different to the methodology involved with stealing the data from your site itself.
In this instance, they are using your website more as a tool, and less as a source.
Using Your Website to Overtly Advertise or Market Their Website or Product
This is pretty straight forward, again further detail can be found below.
In this scenario they have plastered your website with CTA’s (Calls to action) banner ads, and links to their own website or product.
This tends to be pharmaceuticals, adult content, counterfeit designer clothing and a myriad of other products. It changes from hacker to hacker.
You will be able to spot an overt use of your website quite easily just by looking at it.
Using Your Website to Covertly Advertise or Market Their Website or Product
This one is a little different, and is specifically designed to fly under the radar.
If you are not familiar with SEO (search engine optimization) then I will try to outline it in a very simple and quick way.
Google ranks a website (determines the order in which they will be displayed on a results page for a specific keyword) with a very complicated and sophisticated algorithm.
A large factor in this algorithm is measuring the metrics of a website based upon inbound links from another website.
Essentially, if a quality website links to your website, then this helps to tell Google that your website is also quality, and should rank higher. This is similar to the idea that one website vouches for another website.
The problem that a spammer or hacker encounters, is that the website they are trying to rank is generally not a quality website.
In this scenario, rather than do some honest, time consuming and often expensive work, they decide to cheat.
One way they cheat is by forcing entry to a quality website (such as yours) and setting up links that point to their own website.
In theory, this then ‘tricks’ google into making their website more prominent and profitable.
In practice, Google sees exactly what they have tried to do, and then labels the hacked website as hacked.
This could very well be why you are here.
When I first experienced having a website under my supervision being hacked, this is the exact type of hack that they carried out.
I will dig a little further into the nuts and bolts of this, and how you can detect it further down.
Placing Malicious Code into Your Site
If you are here due to a warning that your site may be hacked, then this is potentially not the reason that they hacked you.
Google has a different set of warnings in place for a site that they have detected malware on, including a page in between with a giant red warning sign advising you to reconsider.
If however you have received a malware warning (this will be in your Google Search Console security panel) then the Google resources for hacked sites will be the best resource for you.
The malware may suit many purposes, it can assist in stealing data, gaining additional access around the internet, controlling computers, installing cryptolocking/ransomware software, and much more.
Malware truly is the dark side of the internet.
If malware is involved, then I can strongly suggest you have professional assistance, and make sure that you quarantine your site immediately.
Hacking In Order to Disrupt your Business or Message
I don’t know what your website is about.
Perhaps you sell cookies and glitter, perhaps you vehemently promote hate speech or misinformation.
Maybe you promote or discuss controversial topics, such as eugenics, euthanasia, abortion and so on.
Maybe you promote your own religious or political views.
There are so many ways to make enemies out of ideologies in this world, and the internet has only intensified this in some ways.
You may need to consider that whoever hacked your site was not even trying to make money, rather all they wanted to do was to interrupt your ability to communicate your ideas.
Business Disruption
This is also a darker idea in many ways.
There is always the chance that whoever hacked your site had financial motive, but their means of collecting was to gain a higher market share in your shared industry.
Dwelling on this concept will A) not help you and B) take you down the dark path of accusation, paranoia and contemplative retribution.
I personally wasted quite a lot of my time and energy contemplating whether it was perhaps a competitor who had our site hacked.
This thought process leads nowhere positive.
Focus instead on what you need to do now, and how you are going to be better prepared next time.
Why Would They Hack Your Website
Asking this question is a perfectly natural response.
In fact, as you will learn, it a very necessary question to ask.
Often in life when something horrible happens, we urge ourselves to stay away from such questions as “why would this happen”.
The difference being, often when something horrible happens it is the result of an accident.
In this situation, it is not an accident.
Someone has purposefully gained access to your website and altered it.
Understanding why they would want to do this, and why they would want to do this to YOUR site, is a crucial step in detecting, removing and protecting your site both now and in the future.
Why Your Site in Particular Though
You may be thinking (as I was) that there could be no possible gain in someone hacking your website.
The first thing you need to understand, is that a cybercriminal can gain quite a lot from hacking any website.
We will go over some of the motivations that may have caused this a little further down.
Let’s first of all make sure that you understand why your site in particular was targeted.
Human psychology is inherently hardwired to assess action from correlating stand points of:
- Risk
- Effort
- Reward
- Risk vs Effort vs Reward
Risk Factors
Hackers who decide to break laws know that they are taking a risk. The very nature of a criminal mindset entails that they do not view this as a:
‘Should I break the law’, rather as a ‘what are the chances that I will be caught if I break this law’ as well as ‘what are the ramifications of being caught breaking this law’.
The risks of hacking some sites are always going to be higher than for others.
Depending on the layers of security and detection involved, the chances of them being exposed increase.
Chances are, in the case of your website, they have calculated that the chances of them being caught and severely punished for the hack are rather small.
Effort Factors
Some sites are always going to be easier to hack than others.
Digital security and level of protection are essentially a commodity that can be purchased.
People who assume that their website is not worth hacking, are less likely to be investing in protective factors. Often because they perceive that protective factors come in a one size fits all price category, and that this is an expensive product to purchase.
If a hacker has decided that your site is going to be particularly easy to penetrate, then this may get you onto a shortlist of candidates.
Reward Factors
Dispel any assumptions that you have about what possible reward they could glean from hacking your site.
The reality is they did, and if they didn’t have any direct motivation to do so, they probably wouldn’t have.
There are many valuable metrics that your website has that they may be trying to glean, such as:
- Your website traffic
- Your website authority within Google
- Your website Data
Further down we will go into much more detail about why they may have hacked your site, and then further down again we will discuss what they will have done in each scenario, and how you can find the changes.
Assessing Risk vs Effort vs Reward
Narrowing the hacker’s cross hairs from the estimated 1 Billion web pages on the internet, down to yours has everything to do with how your website correlates to these three factors.
If we start with the assumption that their risk of direct punishment relating to hacking your website is assumed to be 0 (I explain the reason it is 0 at the end of this post), then it becomes more of a discussion of effort vs reward.
Assessing the effort required to hack your site is a simple process of examining what protective measures you have in place, and what known weaknesses you are exposed to.
Protective measures can include:
- Website firewalls
- Hidden Admin Panels
- Dedicated anti-hacking software
Known Weaknesses can include:
- Outdated plugins
- Third party applications with a known security threat
- Knowledge of existing passwords
The next step for a would-be hacker is cross referencing the reward they expect to gain, against the effort required to hack your site.
To have a more visual understanding of this decision making process, let us assume the effort factors and reward factors can each be quantifiably measured on a scale from 1 to 10.
We could then be left with a graph that looks much like this:
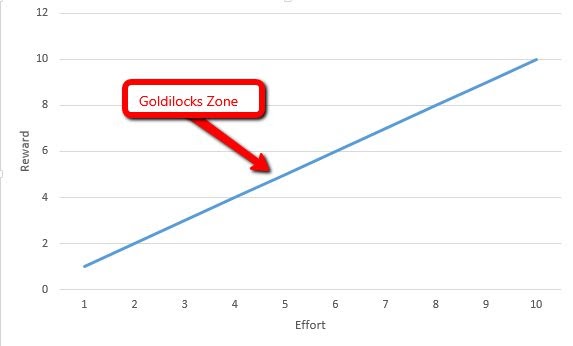
As there is likely to be an escalating difficulty level as the reward level goes up, the golidlocks zone would sit roughly in the middle.
The goldilocks zone references the idea that when facing three options, of varying parameters, that there must be a point in which one of the options is “just right”.
The website is neither too difficult to hack, or too worthless to hack.
What on earth allowed them to spot your vulnerability?
This may still be a lingering question in your mind.
For them to even check how vulnerable your site is, and then check how rewarding a hack could be, they would need to actually find your site and have a look right?
Wrong.
Let’s start with a basic premise:
They are going to select their next hack on a known wordpress plugin that has a vulnerability.
If they know the coding represented by that plugin (which they will) they can perform a search for every website that currently has that plugin.
This can get you on a shortlist.
Depending on what reward they are looking for, they can then filter that list by desirable metrics such as:
- Estimated traffic flow
- Authority of the Domain in Search Engines
This shortens their list of candidates further.
In short, you can be singled out and placed on a “to hack list”, however, the best way to avoid ever being on one of these lists is to take precautionary steps for next time.
In the next section, we will cover some of the reasons that a hacker may be choosing their victims, and what rewards they potentially stand to gain.
Why would the risk be 0 though?
Most hacks come from a different geographical region, using networks that either cannot be traced, or that lead nowhere.
Giant corporations, and even governments often cannot track down or pinpoint who exactly it was that breached their security protocols.
The idea that a small business could do what a government cannot, is ludicrous.
The compounding problem is that even if you narrowed it down to one individual, you would have no real legal means of retaliation or justice seeking.
Different region means different government, a different government means a different legal institution.
Even without contemplating state sanctioned cyber espionage, you need to just accept that wherever the hack came from, it is quite likely that they are both digitally protected from being found, as well as geographically unavailable for prosecution.
How Did They Get in?
In order to make sure that whatever way they got in is not simply a way they will walk straight back in, you will first need to figure out how they got in.
This section will cover some basic principles of how a hacker may have gained access to your site, and some simple processes you can go through to check which doors may have been open and therefore need to be closed now.
Front Doors and Back Doors
Often when people discuss a website hack they talk in terms of front doors and back doors.
Simply put, a front door is an entry point to the secure area that would be normal for someone to enter through.
For example, many sites use the following admin page location: www.example.com
This is an example of a non-visible, yet completely obvious front door.
Another front door is if you display a link for people to log in anywhere else on your website or homepage.
Back Doors are essentially lines of code that have been placed somewhere within your site, that will allow the hacker to walk straight back in whenever they feel like it.
It is quite common for a backdoor to be added after a hacker has first gained access to your site.
They may have gotten in through a front door, but they then make sure that they can get back in once you have closed all the front doors and changed all the locks (aka passwords).
It is also possible that a backdoor has been programmed into your site by someone who was previously working on it for other reasons.
Note: There are legitimate reasons for backdoors to exist, such as for a system admin to be able to reset passwords.
The best way to inspect your site for backdoors is to check which files have been updated or changed recently within your core files, and by which account user. Your webhost should be able to help you with this.
Closing The Doors
An important step in the clean up of your website will be closing every door you can find, and then trying to locate any other potential doors that they could be using.
For the non-technical, you can assist this process by taking a comprehensive look at the users panel within your CMS.
Look for any names of users that you do not recognize, or any users that are no longer working with the website.
After the hack I received on a website I was working on, I went and checked the user panel within our CMS and found that over the years as employees and contractors had finished working on the site, that they never actually had their credentials revoked.
There were user accounts with full admin privileges still sitting there in the names of employees who had not worked on the website in years.
When you find a user account you do not recognize, or that you think is outdated and should be removed; check in with your boss or coworkers, just to make sure that the account should be removed. Then go ahead with the account removal process (this process will be a little different for each person, depending on their CMS).
You will also need to change the passwords for every user across all entry points for your website and website infrastructure, including:
- The hosting panel, or Cpanel
- The server (FTP, SFTP, SSH)
- The CMS (wordpress, magento, drupal etc)
- Your other user accounts, such as social media, google analytics, google search console etc
Remember, it is always safest to assume that all data has been compromisd, and this includes passwords.
If you have been using the same password for your website as you use for other applications and services, then you will need to change these also (e.g banks, paypal, ebay, social media and so on).
Software Vulnerabilities As A Means of Access
There is always the potential that a hacker has gained access through the location of a software vulnerability. For the non-technical people, this is almost entirely a field that needs to be investigated by a professional.
Third Party Software and Applications
You may have heard people often state that wordpress for example is not a particularly secure CMS. The reality is that this is generally due to the fact that vulnerabilities can exist within the extensive plugin range that wordpress users have access to.
When a plugin is not updated, then there is often the chance that a known security vulnerability has not been patched. Often, the main reason a plugin is updated is because a security vulnerability has been discovered and consequently addressed.
When a wordpress user (or any CMS user that uses third party applications and plugins, this is not limited to wordpress) does not update their plugins, yet leaves them within their website; this has the potential to give a hacker a way into their website.
PC Infection
It is possible that your PC, or a PC used by someone who had access to your website, may have been infected by a virus or a Trojan. This PC infection can in turn be used to collect sensitive information that you are entering into your computer, including the log in credentials to your website (as well as every other site you have been logging into).
You will want to ensure that your PC and the PC of anyone else within your company, or anyone else who has access to your site, has a complete and thorough virus scan completed.
Social Engineering
As mentioned in the section involving hackers using your site for phishing, social engineering is a process in which log in credentials are stolen by having a hacked or false version of a login screen displayed to a user.
The user then unknowingly enters their details into the log in fields, and the hackers are able to then record the login credentials.
This is potentially one of the ways that a hacker may have gained access to your website.
Preventing Further Hacks From Occurring

Below you will find some very simple, yet very effective ways that you can help minimize the chances of being hacked again in the future.
Maintain Vigilance Over Passwords
It is important to be very sure about how many people, and who, have access to your website and server at any one time.
You want to limit the amount of people that have FTP and Cpanel access to as few as possible.
You will also want to assess how mnay people have access to your CMS at any one given time.
Making sure that as employees, contributors and contractors leave, that their credentials are also revoked at the same time.
Protect Yourself Against Brute Force Access Attempts
You can download plugins or additional software that will help limit the amount of times someone can attept to enter a password into a login page before it stops letting them try at all.
Another good option for helping to remove the chances of a brute force attack is to make your admin login page less obvious. A vast majority of websites use domain.com/admin as the primary entry portal for an use to sign in.
You may want to consider placing your login screen on a different, less obvious page.
Keep Third Party Plugins and Software Updated
Quite frequently the reason that there is an update on a certain plugin is actually the fact that a security vulnerability has been discovered and consequently patched.
Likewise, always running the most updated software for your server, website, CMS, Operating System and Computer will all help add to the security of your website.
SSL Will Not Prevent Your Site Being Hacked
It is actually quite alarming how many people on the internet are publishing articles which claim that implementing SSL will help prevent an attack.
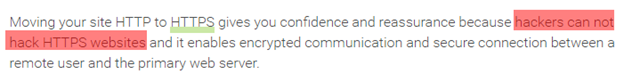
For example, within a very high ranking website, I found this little piece of advice:
This is blatantly false.
HTTPS is a by product of having an SSL certificate for your domain.
An SSL certificate or Secure Sockets Layer, is a process of encrypting data that is being transferred between a server and a client. You can get a much deeper understanding of SSL and HTTPS with this guide from Paul Arneson.
This means that the data cannot be intercepted and subsequently understood.
It has literally nothing to do with preventing someone from hacking your website.
There is a good chance that you are reading this page because you have just noticed something strange on a Google Results page.
This can be worrying to see when you are surfing the net, and even more worrying if it is your own website that this message is appearing under!
I built this page so that if someone finds themselves in a similar situation as I did once, that they will have an easy to navigate and accurate source for the many questions that they will naturally have.
I hope that if you are in the unfortunate situation of recently discovering that your website has been hacked, that this page may bring you a certain level of peace and understanding, whilst also assisting you to solve some of your more immediate problems.